Confidential Infrastructure as a Service (CIaaS)
Introducing the next generation AI security platform built for scalable supercomputing.
Why Confidential IaaS
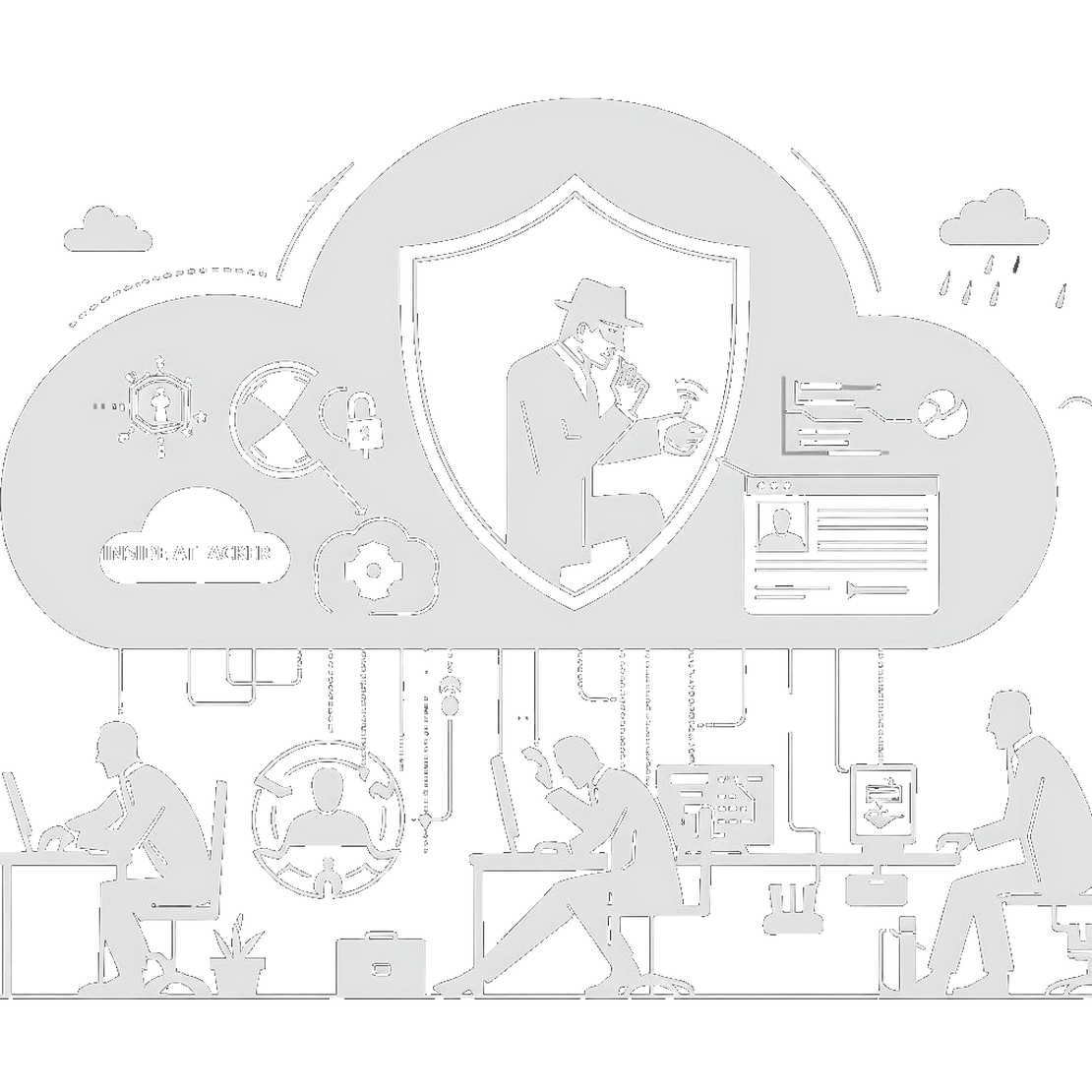
With the rise of generative AI, the attack surface for abusing data, models and computing has increased dramatically. Open source governance done cost effectively is the biggest enterprise priority for CIOs and CISOs.
- Security: Data in motion and data at rest are secure, but data in use remain insecure and prone to insider attacks
- Performance: Homomorphic Encryption schemes can guarantee data in use security, but they are 1000 to 100,000 times slower
- Governance: Enforcement of data usage policies are based on trust, not technology
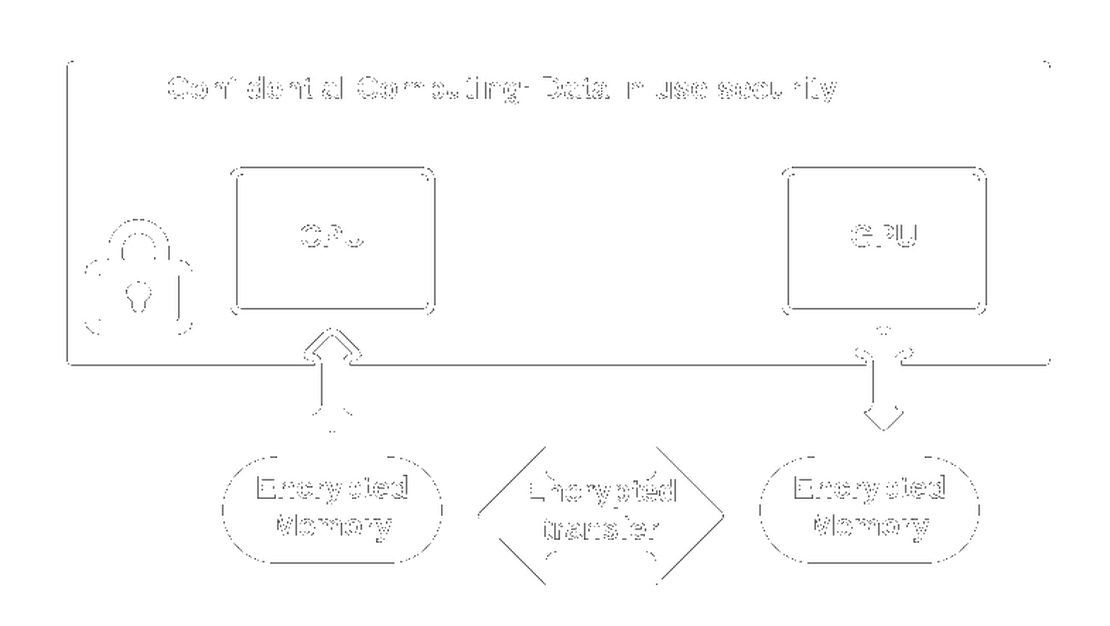
The Vecsec solution
Combinatorial infrastructure of hardware and software enclaves, key management solutions, role based access controls, zero knowledge proofs, homomorphic and searchable symmetric encryption:
- Protect against insider threats – data in the cloud is accessible to the database administrators of the cloud applications or infrastructure via direct access to the database, application logs, and device memory.
- Prevent platform software (i.e., a platform hypervisor) from accessing data
- Protect data from adjacent workloads in a multitenant/user environment
- Protect the integrity of crowdsourced ML models
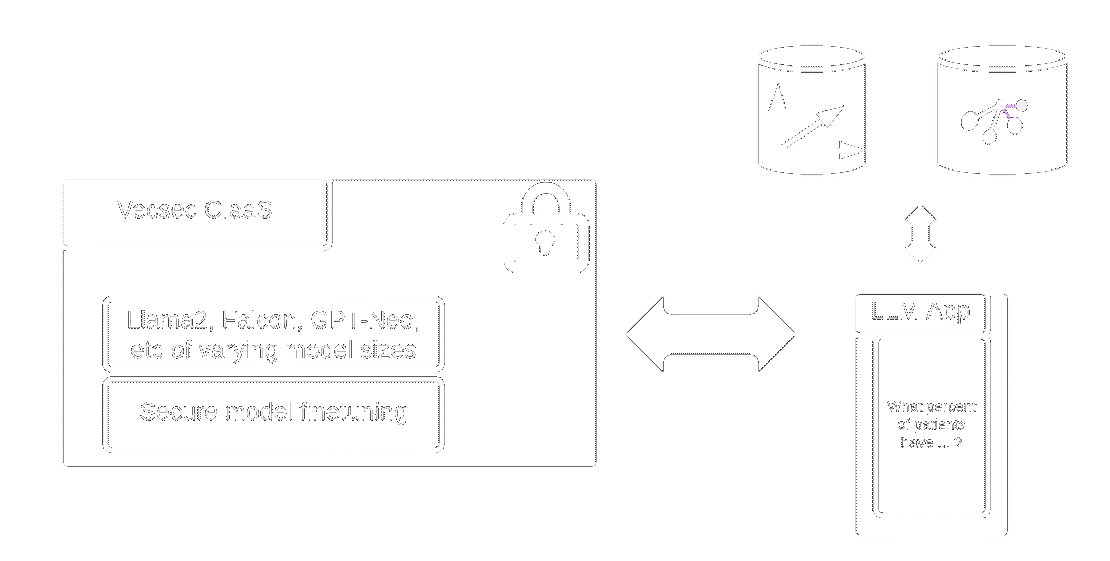
The top reasons to choose vecsec for LLM as a service
With vecsec you can choose the appropriate model that fits your use case in a cost effective and secure way
- Off the shelf support for state of the art open source models such as Llama 2 and Falcon of different sizes
- Cost effective inference and model fine tuning
- Manage your own key and ensure your fine tuned model and queries remain completely confidential
- Confidential computing guarantee: Vecsec has no technical means to decrypt your data